Server
Seal Report includes a Web Report Server to publish your reports on the Web.
On Windows OS, the server must have Internet Information Server (IIS) installed with the current ASP.Net Core Runtime (Hosting Bundle).
On Linux OS, the server must have ASP .NET Core installed (Refer to https://docs.microsoft.com/en-us/dotnet/core/install/).
Note that the Web Report Server may also act as a Report Scheduler if necessary.
Web Report Server Publication Wizard (IIS)
To publish the Web Report Server, run the Server Manager and select the menuIf the site was previously published, use the button Publish only files to update the current site.
Web Report Server Publication on Linux or Azure
Server Configuration
Use the
The server configuration has various properties (Format properties.
Server Scripts
Configure theAudit Script to log the following events in a database: Login, Logout, Report Execution.Dedicated audit Data Sources and reports are provided and may be adapted to query your audit database.
Use the
Report Creation Script to change the default report object when it is created (Report Execution Init Script to modify the report before the execution (Server source code and dynamic assemblies
Share source code amongst your report scripts by saving .cs files in the repository folder Assemblies\Dynamics.The file will be compiled into a .dll assembly that will be loaded automatically.
Sample of .cs source code:
using Seal;
using Seal.Model;
namespace MyNamespace
{
public class MyClass
{
public static int MyInt = 2;
public static void MyMethod(Report report)
{
string message = "this is a test";
System.Diagnostics.Debugger.Break(); //To use debugger in Visual Studio
report.LogMessage(message);
}
}
}
Server is local (No internet) property equals true if your server has no access to the internet.In this case all the Java Scripts and CSS files used in the report result will be loaded from the server.
ASP Session Storage (Pull Request 46)
Session management options
- In memory - stored individually in memory not shared between nodes (default)
- In SQL Server - stored in database, in one table, shared between the nodes.
"SealConfiguration": {
"SessionProvider": {
"SqlServer": {
"ConnectionString": "Server=localhost;Database=Audit;Trusted_Connection=True;TrustServerCertificate=True;",
"SchemaName": "dbo",
"TableName": "CacheSessions"
}
}
}
SQL Server session storage
dotnet tool install --global dotnet-sql-cache
Usage: dotnet sql-cache create [arguments] [options]
Arguments:
[connectionString] The connection string to connect to the database.
[schemaName] Name of the table schema.
[tableName] Name of the table to be created.
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].CacheSessions(
[Id] [nvarchar](449) NOT NULL,
[Value] [varbinary](max) NOT NULL,
[ExpiresAtTime] [datetimeoffset](7) NOT NULL,
[SlidingExpirationInSeconds] [bigint] NULL,
[AbsoluteExpiration] [datetimeoffset](7) NULL,
PRIMARY KEY CLUSTERED
(
[Id] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF,
IGNORE_DUP_KEY = OFF,
ALLOW_ROW_LOCKS = ON,
ALLOW_PAGE_LOCKS = ON,
OPTIMIZE_FOR_SEQUENTIAL_KEY = OFF) ON [PRIMARY]
) ON [PRIMARY] TEXTIMAGE_ON [PRIMARY]
GO
Server Tools
The Server Manager has also
- Check Data Sources checks the current Data Source amongst the database (tables, joins and enumerated lists).
- Refresh Enumerated Lists updates all the values of dynamic enumerated lists. The Data Source must then be saved.
- Synchronize Report Schedules checks all the schedule of the reports in the repository and synchronize them in the Windows Task Scheduler. The schedule is defined with SYSTEM user.
- Synchronize Report Schedules with the logged user performs the same but the schedule is defined with the user running the Server Manager.
System Reports
Several useful reports are available in the Reports/System Repository sub-folder to show the current security implementation, to inventory the reports, to check the reports executions, to query the audit database, etc.System: 100 Configuration - Security Summary System: 200 Audit - Search System: 300 Reports - Inventory
Web Security
Use the
The Web Security defines the login process to the Web Report Server through Security Provider and all the user rights through the Security Groups.
Security Provider
The Security Provider defines how the authentication is done when a user wants to login.
All the default Security Providers are defined in *.cshtml files in the /Security/Providers Repository sub-folder.
A Security Script is executed to define the name and the groups of the user. If the user has no group, the authentication has failed.
Depending on his type, a security provider may have parameters (
Check the
Security Script to have more information.
- Basic Authentication shows a simple user/password authentication from the user name and password of the login window.
- Basic Windows Authentication use Windows authentication to validate the user name and password, and define the groups: Windows group names must match group names defined in the security.
- Database Authentication shows a sample of querying the database to authenticate and get the groups.
- Integrated Windows Authentication is the same as Basic Windows Authentication but relies on the integrated authentication provided by IIS.
- LDAP Authentication shows a sample of using the LdapConnection object to authenticate and get the groups.
- JWT shows how to authenticate a user having a JSON Web Token (JWT) generated by another server sharing a secret key.
- OpenID shows the use of the OpenID authentication.
- No Security just adds a security group to the user.
Two scripts are also available to handle a Two-Factor Authentication:
One Generation Script to generate the code sent by Email or SMS, one Check Script to validate the code.
@{
SecurityUser user = Model;
//Basic authentication script: use the user name and password to authenticate the user and set his name and security groups...
//user.WebUserName -> user name from the login screen
//user.WebPassword -> password from the login screen
user.Name = user.WebUserName; //Display name
if (string.IsNullOrEmpty(user.WebUserName)) {
user.AddDefaultSecurityGroup();
}
else if (user.WebUserName == "userName" && user.WebPassword == "password")
{
user.AddSecurityGroup("aGroupName");
}
else {
//Authenticate and set the groups defined in the security login
if (!user.LoginAuthentication(user.WebUserName, user.WebPassword)) {
throw new Exception("Invalid user name or password");
}
}
}
Test your security provider
Once your Security Provider is configured, user the helperTest a login to fully test a login process with given name and password.
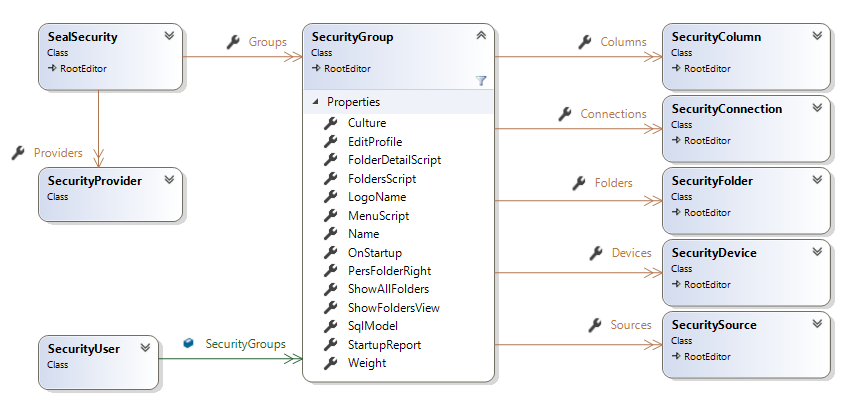
Security Group
After a successful authentication process, the user belongs to one or several Security Groups.
A Security Group allows to configure:
- which repository folders are published for the user,
- if the user can view reports,
- if the user has personal folders,
- if a Startup report is executed at login,
A Security Group has a collection of repository Folders, each folder has a given relative path and right (from No Right to Edit Reports).
For the Reports folders
- Folders: The highest right is used (No right, Execute reports / View files, Execute reports and outputs / View files, Edit schedules / View files, Edit reports / Manage files).
- Personal folder: The highest right is used (No personal folder, Personal folder for files only, Personal folder for reports and files).
- Show all folders: True if one group has this flag set to true.
- Folders, Folder Detail and Menu Scripts are executed sequentially sorted by group name.
-
The options (Edit Profile, Culture, Logo, Startup, Execution mode) are taken from the group having the highest
Weight.
A Meta Column may have a Security tag property. This text can be used to define rights for the designers.
List the current right definitions
The System Report '100 Configuration - Security Summary' generates also a full security summary.To display rights per user, it may be adapted to match the security provider used.
System: 100 Configuration - Security Summary
Custom Publications
In addition to the security applied on report folders, dedicated scripts (properties of a Security Group) allow to modify the reports published to the logged user.
-
Folder Script: Optional script executed to define/modify the folders published in the Web Report Server. -
Folder Detail Script: Optional script executed to define/modify the reports published in the Web Report Server for a given folder. -
Menu Script: Optional script executed to define/modify the reports of the logged user.
If the user belongs to several groups, scripts are executed sequentially sorted by group name.
Folder Detail Script sample to filter 'Charts' reports in the /Samples folder:
@{
SecurityUser user = Model;
if (user.FolderDetail.folder.path == @"\Samples") {
//Sample to filter reports
user.FolderDetail.files = user.FolderDetail.files.Where(i => i.name.Contains("Charts")).ToList();
}
}
Startup Report
Once logged with the Web Report Server, a startup report defined in the Report executed on startup property of a Security Group can be executed automatically.
This allows to fully customize the login page for given users.
Check the following sample Startup Reports
- 40-Startup Report: Defines a Welcome page with several options to execute reports and to browse specific folders.
- 41-Startup Folder: Forces a specific folder after the login and disable most of navigation and execution links.
Seal Web Interface
Once installed, the Web Report Server offers a simple interface to ease the integration of Seal Report into existing web sites.
Contribute to Seal Report
Enhance the documentation and samples
Want to share your experience or to add a new topic ? Something is not clear in the documentation ? Do you have an interesting recipe ?As the site for the documentation is part of the solution, you are welcome to Pull a Request at GitHub.
Add translation files
Do you have a translation file not yet supported by Seal Report ?As the translations are part of the project, feel free to Pull a Request at GitHub.
Sponsor the project
If you are using Seal Report in a business application, please consider to sponsor the product to ensure its maintenance, quality and independence.Please check Support and Sponsor.
And more...
You are also welcome to help us in several different areas:- Beta testing.
- Libraries of Data Sources and Reports on standard databases.
- Additional View templates.
- New features development.